[ad_1]
Android 12 has a new Privacy Dashboard that makes it easier for users to check up on and manage the permissions on their devices. Jack Wallen gives you a peek into this new tool.
Image via ZDNet
Android 12 is poised to be one of the most substantial upgrades to Google’s mobile platform to date. Not only will it completely redefine the Android UI/UX with Material You (and it’s really cool), the upcoming iteration of the OS brings some long overdue features to the table.
One such feature places app and device permissions in a single, easy-to-use dashboard, allowing users to not only have better control over permissions, but have a much easier time in managing those permissions.
The feature is called the Privacy Dashboard, and it’s something every Android user should be anxious about.
SEE: Electronic communication policy (TechRepublic Premium)
What can you do with the Privacy Dashboard?
As you probably assume, the Privacy Dashboard is all about privacy—that means it’s about permissions. When you open the Privacy Dashboard you’ll get an at-a-glance at what services or hardware has been accessed the most in the past 24 hours (Figure A).
Figure A


In the past 24 hours, the mic, the camera and location services have been used.
The big question is “What do you do with this information?” Consider this: you open the Privacy Dashboard to see the mic and the camera have been used in the past 24 hours, only you haven’t used any apps that required those two permissions. You could have found yourself in a compromised situation and should immediately take action, as some malicious action could be afoot.
That’s not to make you paranoid, it’s to empower you. If you see the Camera has been used in the past 24 hours, tap on the Camera listing and it will show you exactly which app used the service (Figure B).
Figure B
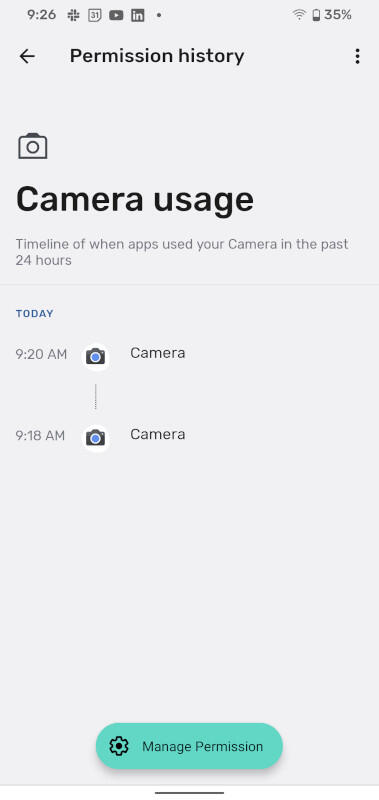

Fortunately, in this case, the Camera used the Camera service, so everything is on the up and up.
If you find some other app used the camera service (one you have used in the past 24 hours), tap Manage Permissions and you can then revoke the permissions of the app that used the service, should you deem it necessary(Figure C).
Figure C
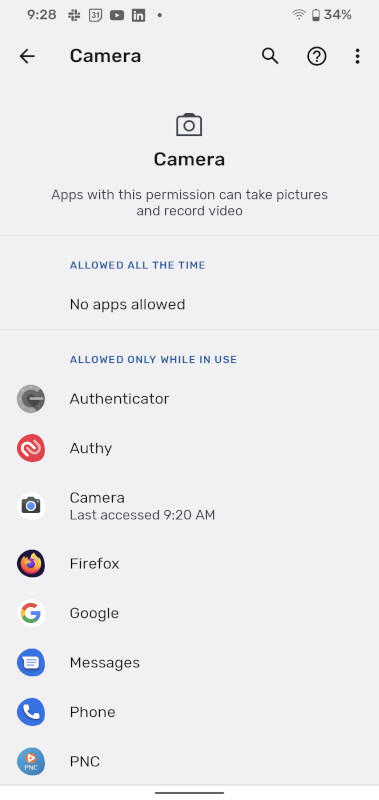

The listing of all permissions associated with the Camera on Android 12.
The one thing you must be careful of is blank disabling of permissions for a service or sensor. Disable the wrong permission and you could render an app or service broken. When you do suspect something is amiss, your best bet is to do the following (which only applies to Android 12):
- Pull down the notification shade twice.
- Tap to disable Mic and Camera access, as well as Location.
- Go back to the Privacy Dashboard.
- Find out what apps have accessed those devices and sensors.
- Do a quick Google search to see if those apps should have access to the services/sensors in question.
- If not, remove permissions from the app. If so, do nothing.
If you find the app in question is legit, you can go back to the Quick Access tiles and re-enable Mic, Camera and Location.
And that’s how the Privacy Dashboard will work to help you stay on top of permissions on your Android device. Thing is, this is an important step forward for Android security, but it’s up to users to make the effort to regularly check on what’s happening on their devices.
The developers have gone a long way to make everything automatic, but no platform is 100% effective at stopping malicious behavior on its own. Once you have Android 12 on your device, make sure to regularly check out the Privacy Dashboard. Think of it this way: if you’re only checking it out because you believe something is amiss, it might be too late.
Subscribe to TechRepublic’s How To Make Tech Work on YouTube for all the latest tech advice for business pros from Jack Wallen.
Also see
[ad_2]
Source link
